Security in a world of IPv6 and Bitcoin
We are starting to move to IPv6 and the cloud. Right now, the uptake is minimal at best with very few early adopters for all of the hype. That said, the climate is changing. Soon, IP addresses...


We are starting to move to IPv6 and the cloud. Right now, the uptake is minimal at best with very few early adopters for all of the hype. That said, the climate is changing. Soon, IP addresses...

Ron Coase made several errors in his theory of transactional processes in economics. Most critically, he has failed to note the value of property. Property rights include the right to have and...
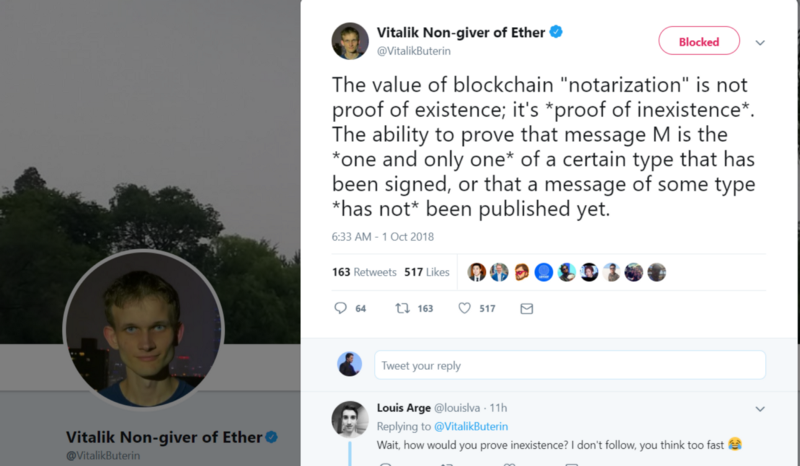
I was forwarded one of the most ignorant concepts of what Bitcoin (and for that matter Blockchain) is about earlier today. This would be a part of the problems that are associated with the false...
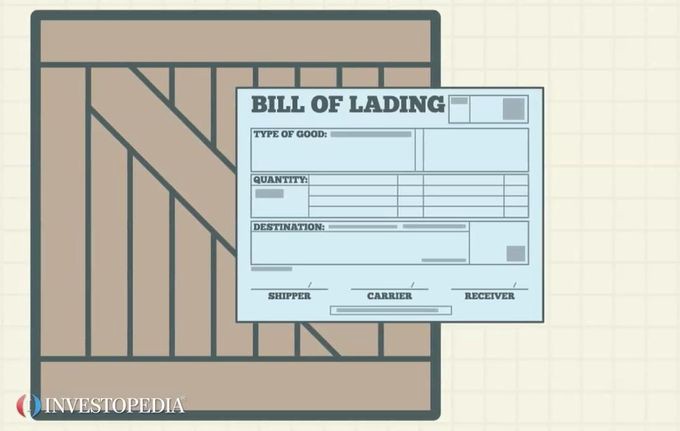
Introduction The Bill of Lading is a document unique document as its negotiability fulfils several purposes. These documents have led to a range of instruments and conventions within international...
There are a number of contractual issues that used to be associated with e-mail that apply to Bitcoin today. There were for example, numerous debates over the applicability of the postal rule for...

Some are treating the scenario of mining proceedings as a forward memory — remembering what HAS NOT happened. If you have the system as memoryless, the miners have to have an expectation that...
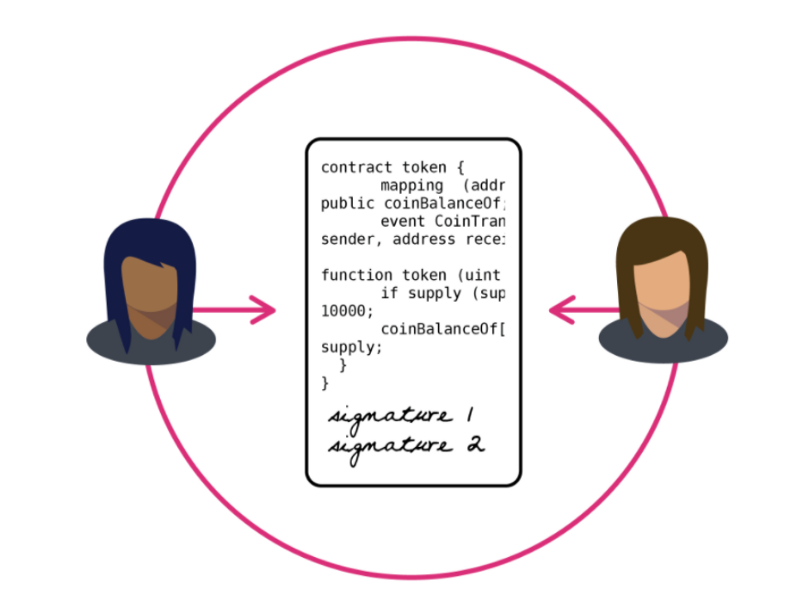
When contrasting contractual principles, it is clear that where a contract is not required to be in writing (Columbia Law Review, Apr., 1929 Pp. 497–504; Columbia Law Review, Jun., 1907, pp....

The postal acceptance rule states that where an acceptance is to be sent by post, the contract associated with that acceptance is considered as concluded at the moment of posting the letter, not...

To an extent all software is a black box. As a consequence, the quote concerning Bitcoin needing to be open source and a means to “free us from government” that is is commonly made is false and...
There is a small correlation between the effects of security and simplicity. This use of complexity for its own sake (See ETH, Core etc) will not add and may remove security. Likewise, simplicity...