We are starting to move to IPv6 and the cloud. Right now, the uptake is minimal at best with very few early adopters for all of the hype. That said, the climate is changing. Soon, IP addresses will be on everything. More, Bitcoin (BCH) will be the exchange system for everything.
Network systems work on an exponential growth curve. Things are exponentially less expensive each year and incrementally more powerful. This will drive applications and uses that people have not even thought of. The following are ideas that have serious money already behind them, and are just a few years from deployment:
- Disposable communication tablets. Basically these could be dropped in places such as Iran, and allow for communications no matter what the incumbent government tries to filter. Think $1 devices.
- Milk, Coke cans, and more in supermarkets with IP addresses and RFID. Why, well first, as they can integrate this with smart appliances, but more importantly, with merchandising and stock control. Who needs to do stock take when the store tells you what it contains.
- Light bulbs with web and IP addressing. Well actually these are already available.
The thing is, there are many reasons why IP addressing will be used up quickly, and these are but a few. That is one reason why we will move to IPv6. Mobility and security are others.
The catch-cry of the 21st century will be, Anytime, Anywhere.
Done correctly, IPv6 can make for extremely secure networks. Right now, using Group Policy and a number of other tools, if you have Linux or Macs, it is already possible to make a secure mobile network. It is more difficult under IPv4 due to the constraints on the protocol and the nature of DHCP (against DHCPv6)
As much as I like Linux, I will just talk on Windows for this post, as it becomes far too complicated to start going into all the possibilities when Linux, Macs, Windows, and other devices are involved. Microsoft have already published a number of good IPv6 implementation guides too. More, they have detailed processes for implementing IPv6 through Group Policy. This can be done using Linux and other devices, but the economy of time constrains us all.
Secure server
In the domain world, Windows allows for the simple deployment of secure-server and client-trust models. This can also be achieved using Workgroups, but like with Linux, it is more complex.
Using Group Policy, you can set a client to only talk using encrypted sessions and only to trusted servers.
Why restrict clients this way?
In a large organisation, client peer-to-peer communications can be a means of malware dissemination. There is rarely any real need that cannot be achieved on the server to have clients talking to clients over the network directly. Rather, they should be controlled via a server.
What this can allow is that only authorised client hosts are allowed to communicate with servers.
In an organisation, even mobile users can be forced to communicate to company servers. This is where the cloud becomes important. With disk encryption, IPv6 with IPSec enabled, and the right controls each and every host is firewalled.
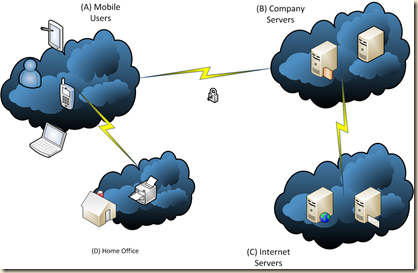
A mobile user (A) can be restricted to communications with only allowed systems (such as a home office (D), and the corporate servers (B).
All attempts to connect to the system with an untrusted host will be dropped, as the host attempting this will not (we are assuming that keys have not been compromised here) be allowed to communicate through policy and host firewall rules. As said, this is simple using Group Policy.
Here, the client host can be restricted to connecting to the organisational proxy server and no more.
Using DaaS (Desktop as a Service) with a mobile tablet makes this even more secure if done correctly. The desktop can be configured to be accessed only from selected tablets with a key, and at best the loss of a tablet will provide only a key to the remote desktop which still needs to be authenticated to.
This restricts local access to the host as the “desktop” is stored in a data centre. The user cannot use local escalation attacks based on physical access to the system, as they are never actually on the system.
More, if the user loses a tablet or other device, they are not actually connected to the system and files, and the loss of the tablet will not lead to a loss of data (if configured correctly).
As the desktop is configured to only talk to the tablet and the organisational servers, and all communications are encrypted, the location of the user does not actually matter, and they can be truly mobile (as IPv6 allows). More, this allows the organisation to control access to the Internet through organisational proxy and email servers. With flags in IPv6, we just happen to be able to integrate the payment of all this.
As strange as it may seem, a well defined and deployed cloud and IPv6 system can actually be far more secure than the traditional crunchy shell-firewall model.
Now, with IPv6 jumbo blocks and BSV as a payment channel… We have a path to Internet of Value on demand.