Cryptography can be used to limit access, and may be restrictive. When a file is encrypted, it can only be accessed with the key. As such, it can act outside of state control and allow individuals to transmit illegal information rather than merely protect privacy. The aims of the individual and what they’re doing using cryptography dictate how the outcomes of any action involving encryption apply. In modern banking, encryption is essential to ensure the security of systems and that they cannot be intercepted. Trusted third parties are required to hold certain access to data that is being encrypted, to ensure that anti-money laundering (AML) provisions are not being breached. Bitcoin differs insofar as it allows individuals to hold and maintain identity data without having to encrypt transaction logs and exchanges.
Bitcoin is not encrypted. All transactions are conducted, exchanged, and validated in clear text. Although it uses digital signature algorithms, no encryption is used at any point. A hash presents not a cryptographic algorithm, it is a secure method of producing an index to a file, one that can be used to validate integrity. File integrity allows individuals to ensure that nothing has been changed, in a manner analogous to a checksum — but with far more security and accuracy.

Consequently, as Bitcoin presents clear text, there is nothing that can be used to stop alterations on the blockchain. What people do not understand about an immutable ledger is that you can make changes by adding new records. Doing so does not remove the old records. It only adds additional records. The same form of accounting is legally mandated across all public companies in the US.
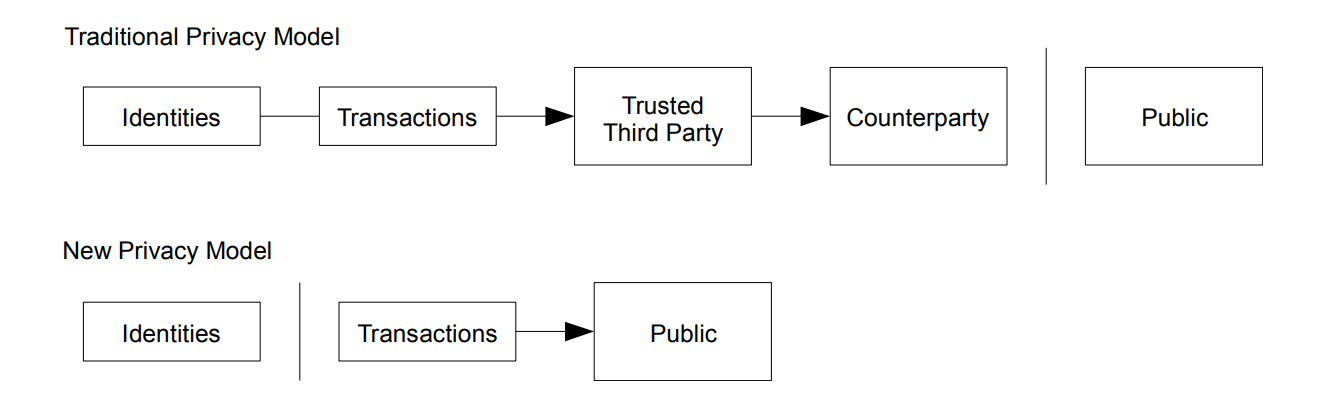
The traditional banking model required that all transactions would be exchanged with counterparties and trusted third parties. Any breach of the firewall isolating the trusted third party and the public led to a catastrophic breach of security. Bitcoin differs as transactions are maintained openly. Identity systems can be constructed within Bitcoin, by, for example, using either traditional PKI-based systems that are linked to the blockchain itself or more advanced key-distribution methodologies, ones we have been working on and patenting. But at no point did Bitcoin alleviate the need for identity management.
There is a belief that Bitcoin does not require identities or the recording of customer details under customer due diligence rules, which is false. Any time you transmit funds in excess of USD10,000 [1], you fall under requirements of US law. Any time you set up business relationships involving transactions worth more than EUR15,000 [2], there are requirements to ensure that customer due diligence has been conducted. Some people think that Bitcoin would be immune to such regulations. They are, sadly, deluded. When I created Bitcoin, I sought to produce a platform that would act within law and simplify many of the processes associated with the need to transmit information to payment intermediaries who would be required to hold large databases that could be easily compromised. Bitcoin distributes such information so that it can be maintained by individuals both on- and off-chain, creating a far more secure system as the cost of attacking increases with information being distributed to the edges of the graph.
The issue I saw with the traditional banking model or ones involving trusted third parties stems from the security problems associated with organisations such as Target, that allowed millions of individual records to be leaked. In the white paper, a solution is described where access to information can be limited to solely the individuals engaging in an exchange.
The use of the word anonymous in the white paper reflects the definition of it presented in Black’s Law Dictionary:
ANONYMOUS
Nameless; wanting a name or names. A publication, withholding the name of the author, is said to be anonymous. Cases are sometimes reported anonymously, t. e., without giving the names of the parties. Abbreviated to “Anon.”
The Black’s Law definition of anonymous implies not that under its realm, identity does not exist. Rather, using hierarchical methodologies [3], it is possible to leverage the homomorphic properties of ECDSA. A jointly calculable value can be safely added to each key, allowing a registered identity key to remain outside of the public exchange yet be provably linked to the identity of the individual engaging in commerce across Bitcoin.
Under Bitcoin’s new privacy model, the individual parties hold the identities of each other, and are, in other words, able to fully determine who they are dealing with. The public, on the other hand, may see that exchanges of information are being recorded on the blockchain, yet does not have the bits required to link information and transactions to the individual parties. Derivative implementations of Bitcoin such as in the form of systems like BTC, under Bitcoin Core, have completely broken the privacy model of Bitcoin, in an attempt to create an anonymous system that will facilitate crime using dark web servers. Yet, the built-in traceability associated with Bitcoin precludes such a scenario.
As was noted in my white paper for Bitcoin, “As an additional firewall, a new key pair should be used for each transaction to keep them from being linked to a common owner”. Doing so does not preclude the use of identity-mapped keys. ECDSA was selected because of its additive properties. It allows individuals to keep a base identity key and continue to transact with one another in a way where they can maintain complete privacy from the public, yet all of the requirements of a trusted third party and identity management are being fulfilled. In such a system, businesses and individuals can conduct customer due diligence and maintain all of the records securely, without them ever being leaked to the public. Here, identity information can be maintained by the owner, the individual transacting.
As a system that is not encrypted, Bitcoin precludes nodes or exchanges from interfering with actions from courts and government — at no point was Bitcoin ever intended for such purposes. To be free, it is essential that individuals transacting in an open market are protected from criminals and associated deeds.
Because Bitcoin is not encrypted and all transactions are publicly broadcast, every transaction on Bitcoin can be followed. If law enforcement were to obtain a freezing order, it could be applied to both an individual key and any transaction that branches from the key. New means of tracing and following provide a level of granularity that, while maintaining the privacy of honest individuals, has not been available to law enforcement in the past. Without the use of encryption on-chain, Bitcoin precludes any interference with such a process. If a court order was granted against an individual key, normal tracing operations and the proceeds of crime legislation could be enforced. The requirements to maintain complete identity records around individuals transacting in coins (bitcoin) beyond certain amounts, corresponding to the above, ensure that individuals who do not maintain adequate documentation do not, as such, have the right to claim the tokens or bitcoin they hold as their own.
When bitcoin has not been used as money, and when it has been sourced without conducting adequate due diligence, as was the case in Armstrong DLW GMBH v Winnington Networks Ltd (Armstrong) [4], merely owning keys, while having bitcoin registered on the distributed registry that is the blockchain, is insufficient to prove ownership of coins. The Armstrong case was one of inadequate due diligence. It involved carbon credits or EU Allowances (EUAs), which are registered as digital tokens on a distributed registry or ledger. The registry used to distribute carbon credits is one that facilitates the trade of tokens “as commodities”, where “carbon credits are ultimately entirely “virtual”, making them vulnerable to the possibility of double counting and other forms of forgery”.
In part, I modelled the system that would come with Bitcoin upon the idea of EU Allowances. One reason for doing so was that I had planted a large forestry program, and from 2005 sought to register carbon credits and trade them, based on the timber I had been planting. The system was inefficient but based on a distributed network of registries, with each individual European member state holding its own registry, that needed to be updated across all other member states. In effect, each member state may be seen as being analogous to a Bitcoin node.
Following the problems with the system, and subsequent problems in being able to register and authenticate transactions, I decided to build my own system, a system that would enable the complete tracing of a virtual token without “double counting”, or, as it is called in the Bitcoin white paper, “double spending”. In the fullness of time, in its complete implementation, Bitcoin is a system that significantly limits insider trading, tax evasion, money laundering, and cybercrime.
Today, a single registry, the EU ETS Union Registry for the EUAs, is provided by the European Commission under Regulation No 389/2013. It was the response to several successful hacking attacks, in 2010 and 2011, on various national registries that had documented emissions. The attacks had led to the temporary suspension of the registries maintained in each member state, pending the implementation of minimum security requirements. The Regulation sets out various technical security requirements, bringing the Registry in line with the security standards used in the financial sector. Using Bitcoin, registries could be secured in a manner that would not allow them to be attacked as they were between 2010 and 2011.
The Armstrong case was held for the claimant and against Winnington Networks Ltd’s defence of a bona fide purchase without notice. The defence was defeated through the knowledge that Winnington Networks Ltd had not engaged in complete and adequate due diligence or maintained customer records, which meant they had not acted in good faith. As with Bitcoin, the registry does not present proof of ownership. It is a record of possession. For ownership to be perfected, the exchange of tokens using Bitcoin needs to involve the sale to a bona fide purchaser, without notice of who has followed the chain of ownership, that is recorded on the ledger and can be verified using identity and customer due diligence methodologies. For small transactions, the scenario is not onerous at all. Any time large transactions are carried out, it is necessary to ensure all requirements around due diligence are followed.
It should be clear that owning keys does not equate to owning bitcoin. Keys in Bitcoin present a means of controlling access and updating the ledger, yet not ownership of the tokens themselves. Ownership of the tokens follows standard property rights, and if you don’t do your due diligence, it doesn’t matter that you have your keys; you may not own your bitcoin.
Notes
[1] See https://www.ecfr.gov/cgi-bin/text-idx?SID=f7495bb4cb9f4181f1505d475bb7fb22&mc=true&node=se31.3.1010_1100&rgn=div8 (retrieved on Feb 20, 2020).
[2] See https://www.lawsociety.org.uk/support-services/advice/articles/customer-due-diligence/ (retrieved on Feb 20, 2020):
Under regulation 27 of the Money Laundering, Terrorist Financing and Transfer of Funds (Information on the Payer) Regulations 2017 (MLR 2017) you must carry out CDD measures when:
- establishing a business relationship
- carrying out an occasional transaction that amounts to 15,000€ or more
- you suspect money laundering or terrorist financing
- you doubt the accuracy or adequacy of documents or information previously obtained for CDD
If you’re required to carry out CDD measures, you must:
- verify your client’s identity based on a reliable independent source (such as a passport)
- identify where there’s a beneficial owner who is not the client and take reasonable measures to verify their identity and to understand the ownership and control structure of a legal person, trust, company, foundation or similar legal arrangement
- assess, and where appropriate obtain information on, the purpose and intended nature of the business relationship or transaction
[3] See https://patentimages.storage.googleapis.com/e9/d4/1a/644d344019a178/EP3268914B1.pdf (retrieved on Feb 20, 2020).
[4] Armstrong DLW GmbH v Winnington Networks Ltd [2012] EWHC 10 (Ch). Jan 11, 2012.