This document is intended to provide an overview on Decentralised Autonomous Corporations (DAC) based on the blockchain technology. Note, Bitcoin is covered by the ticker BCH. BTC is not Bitcoin following the addition of SegWit.
In this post, we provide definitions of:
(i) DAC,
(ii) Secure Multiparty Computation — a secure multiparty protocol for authorising transactions,
(iii) Autonomous Agents — a set of computer programs that carry out some set of operations on behalf of users.
I will conclude the post by an application to financial portfolio management.
The best part, nothing of this or anything like it will be on anything other than Bitcoin (BCH). Not ETH, not BTC, not some sham coin. No DOA, no PoS… legally valid entities.
Decentralised Autonomous Corporation
A Decentralised Autonomous Corporation (DAC) is a visualised corporation without the need for any central point of control, with a certain agenda, business plan, and protocol. It can be a corporation, a trust, or a company. The decisions can be made in advance and for many simple tasks no human interaction is needed.
Note: all entities are owned by people, and this means that the capital and decisions are associated with a human party.
DACs can run with only minimal human involvement, and are defined by code and software. They aim to be autonomous in the sense that they implement mechanisms for self-regulation. It is possible that a system can be created that operates, once it is fully operating, such that it no longer needs further input from its creators.
DACs are distributed. There is no failure point that can be attacked, and DACs cannot be shut down, or even modified to make them send all of their money to an attacker’s account.
DACs necessitate a network of Autonomous Agents (AAs) which perform functions within an environment to achieve goals, without being directed to do so. One example of an AA is a computer virus; the virus survives by replicating itself from machine to machine without deliberate human action.
DACs generate Bitcoin addresses. DACs construct and sign transactions. Thus, a system of signing transactions that can be computed in a decentralised way is needed.
The first solution is multi-signature addresses; given a set of AAs, for example 1000, we generate a 501-of-1000 multi-signature address between them. The problem is the transaction would be too large. The maximum size of a standard transaction is 10,000 bytes [1]. Each signature is about 70 bytes [2], so 501 of 1,000 signatures would make a 35,000 bytes transaction. The second solution is secure multiparty computation.
Secure Multiparty Computation — Key Sharing
Secure Multiparty Computation (SMC) protocols allow a group of mutually distrusting parties to compute a joint function on their private inputs. SMC is a technique for protecting confidential data. The secret is divided into parts — shares. These shares will then be distributed among the parties. In order to reconstruct the secret, a certain predefined set of shares — the threshold k — must be combined. Gaining access to less that the threshold of distinct shares shall give no information about the secret.
Let s be a secret value and n share s(i). We have a k-out-of-n secret sharing scheme, if the following conditions hold
- Correctness; knowledge of any k or more shares of s makes the secret easily computable,
- Privacy; knowledge of any k — 1 or fewer shares of s leaves the secret completely undetermined (in the sense that all its possible values are equally likely)
We consider the case where a large number of AAs wish to securely perform some complex distributed computation on their inputs, i.e. signing Bitcoin transactions. In this case, we use Shamir’s secret sharing scheme (SSSS) [3, and references therein], which uses the idea that k points are needed to uniquely define a polynomial of degree k — 1.
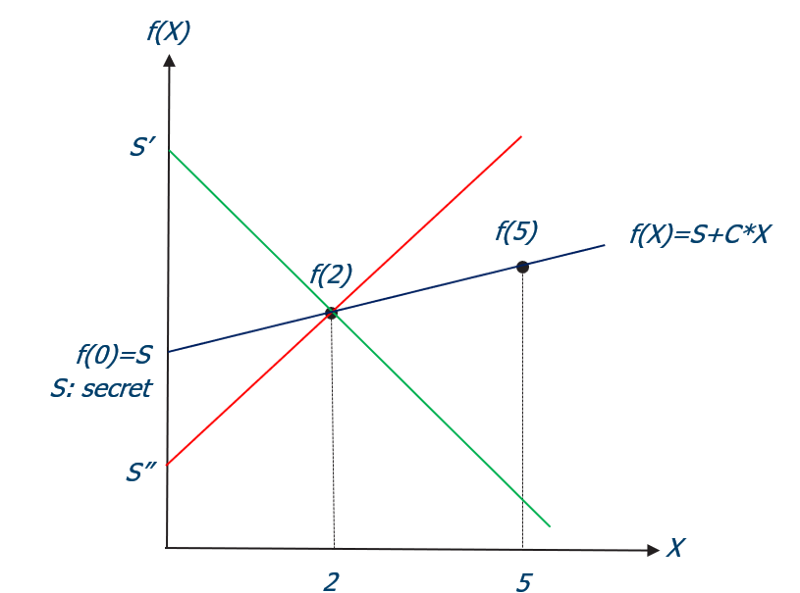
Shares in SSSS have two values — an index and the evaluation of the randomly generated polynomial on that index — (i, f(i)). The indices have to be unique to each party and we cannot use zero as that would reveal the secret f(0)=s. To create the shares, we choose n random points on the polynomial (x, f(x)). These points are then distributed to the parties. The coefficients will be chosen randomly and the free member is equal to the secret. Figure 1 illustrates Shamir’s scheme using a random 1-degree polynomial.

A nice property of elliptic curves is that if a (k,n) threshold scheme with polynomial interpolation is set with the public key, the private key can be recovered from k of the n pieces exactly in the same way as the public key.
Autonomous Agents (AAs)
An Autonomous Agent is a computer system that is situated in some environment (e.g. the Internet), and that is capable of autonomous action (e.g. buying, selling) in this environment in order to meet its design objectives.
AAs are purely software. They receive and execute instructions written in a Practical Agent ProgrAmming Language (PAPAL). PAPAL is the agent programming language.
AAs do not have the capabilities to manufacture a product, write code, and develop hardware. They require actors in the physical world for this purpose, called contractors.
Herein we define different classes of autonomous agents: voting-AAs and task-AAs.
Autonomous Interface Agents (AIA)
Autonomous interface agents can make real-time suggestions to users based on a simple keyword-frequency information retrieval measure.
For example, an autonomous interface agent may observe that a user is interested in or hold shares in the bank sector, and it may suggest to him that he invests in the metal sectors (assuming that both sectors are independent). The AIA enquires another AA to look for an asset that is not highly correlated to the bank sector, then a pop-up window appears showing the correlation and other indicators between the gold price and HSBC share price.
Voting Autonomous Agents
Voting-AAs are agents who are empowered to vote.
At the deployment phase, the DAC issues N tokens to raise money (via Dominant Assurance Contract?). The tokens represent the company shares. The tokens grant its holder ownership and voting rights.
The DAC issues N shares to raise money — if goal not reached then repayment (Dominant Assurance Contract)
(i) Tokens are used to represent company shares and necessitate a smart contract for revenue sharing [Should the revenue be automatically shared as it is earned in realtime? Should the share/token hold a piece of DAC private/public keypair, i.e. (x, f(x)) -> if someone holds k pieces, it is equivalent to a 51% attack]
(ii) The share price can be time dependent, like easy-jet tickets
The coloured coin transaction contains a pair or multiple pairs of (x, f(x)). Tokens can be exchanged, and new share owners request new pairs (xnew, f(xnew)). Previous (xold f(xnld)) should be removed from the DAC database, and (xold f(xnld)) cannot be accepted as a valid share.
Task Autonomous Agents
Task-AAs search for vacant tasks guided by its own preference orders over available tasks. It selects a contractor and submits the contractor’s proposal for voting either to the voting-AAs or to the DAC members. DAC members can review the contractor’s proposal and send their share (x, f(x)) to the task-AA [Prior to deployment, the entity distributes the shares between the AAs]. If the task-AA collects k shares, it submits a smart contract on the blockchain representing the proposed project. There is a set time frame to vote on any given proposal. After this time, the proposal is closed.
Voting for Proposals
Shareholders of a DAC cast votes weighted by the amount of tokens they control. Within the contracts, the individual actions of members cannot be directly determined. There is a set time tp to debate and vote on any given proposal. The time frame is set by the function-AA. After tp has passed, any token holder can verify that the threshold value k has been reached, i.e k shares have been collected. If this is not the case, the proposal is closed. A minimum number of shareholders can also be required for the vote to be valid.
In order to ensure transparency and before a vote can take place, a contractor profile should be presented to the voting-AAs and to the shareholders. Table 1 shows an example of a contractor/company profile.

Shareholders can vote using the (hypothetical) platform MyVote or they can delegate their voting power to the voting-AAs. In the latter case, shareholders provide information to voting-AAs using the platform BlockID. to provide information that will be latter used by the voting-AA.
We propose two voting methods:
- using a voting platform
- relying on the voting-AAs
A Blockchain Based Voting Platform
Allowing a Vote DAC creates a platform which utilises blockchain technology to allow voters to vote at home and in their own time. By casting votes as transactions, one can create a blockchain which keeps track of the tallies of the votes. This way, shareholders can agree on the final count because they can count the votes themselves, and because of the blockchain audit trail, they can verify that no votes were changed or removed, and no illegitimate votes were added.
BlockID — A Blockchain Based Platform for Digital Identity
BlockID is a concept for a blockchain based identity service that allows shareholders signing up for an account and the DAC submitting questionnaires, see Table 2.
A digital identity is comprised of characteristics, or data attributes, such as the following:
- Date of birth
- Social security number
- Medical history
Identity theft is rampant on the Web digital identity authentication and validation measures are critical to ensuring Web and network infrastructure security in the public and private sectors.
BlockID can be used as a driver licence, passport, credit card, apartment keys etc…

Decision Making and voting-AAs
If shareholders decide to not be involved in the decision making, they can rely on their voting-AA. For voting-AAs to achieve their function, they require access to the questionnaire completed by the shareholder, and the decision of the voting-AA is handled by one or more classification algorithms. In the following, we propose a simple solution using a decision tree algorithm. But, any suitable machine learning algorithm, e.g. neural network or SVM, can also be used.
Option Decision Tree are similar to regular decision trees, except that they can contain option nodes in addition to regular decision nodes and leaf nodes. Option nodes allow multiple branching instead of a single branching per node.
Figure 2 depicts part of an actual Option Decision Tree.

Application: Digital Asset Management (DAM)
DAM is an application of a multi autonomous agent architecture to the problem of financial portfolio management. The multi autonomous agent system approach (i) requires the coordination of several component tasks (gathering information, interpretation, prediction, etc). The system should be reliable; if one or more agents fail, the system will continue to function. AAs are designed with redundant capabilities and/or appropriate coordination mechanisms. Thus an unresponsive agent is not a problem.
The DAM system deploys a number of different task-AAs:
- Breaking news-AAs gather information from breaking news articles from the web. These agents track and filter news stories and decide if they are so important that the user through the interface-AA and/or other AAs need to know about them immediately.
- Stock tracker-AAs gather stock prices in real time. Their activities are initiated, either by a user or an AA, through queries or through monitoring information sources for the occurrence of a particular pattern; e.g. a particular stock price has exceeded a predefined threshold.
- Model-AAs build mathematical models using standard approaches (e.g. ARIMA), data mining techniques (e.g. neural network), and complex stochastic models to try to predict the near future in the stock market.
- Risk-AAs evaluate portfolios for financial risk using a stock market risk measure.
- Interface-AAs interact with the user receiving user specifications and delivering results. They utilise user specifications to guide system coordination. Interface-AAs display a comprehensive summary of the user’s portfolio.
- Trader-AAs vote based on their trading strategies.
- Etc…
A simplified representation of the DAM architecture is shown in Figure 3.

DAM has three primary purposes. First and foremost is the making of trading decisions, secondly is the submission of those orders to market exchanges, and thirdly is the management of those orders post submissions [Portfolio management is not the core of DAM, and it can be outsourced to another system that integrates DAM].
Purpose #1 — Make trading decisions
Trading decisions are made according to a particular strategy. Trading strategies are generally based on one or more of the following techniques:
- Quantitative analysis — constructed using fundamental indicators and mathematical basis of price movements and historical/current data.
- Event based — based on analysis of historic and current events often profiles from textual news data
- Sentiment based — constructed using indicators that capture market sentiment.
Such strategies can be derived using machine learning algorithms.

Purpose #2 — Submit orders
Trade orders are requests to buy or sell securities. The purpose of DAM is to submit appropriate trading orders that are accurate, timely, and transparent. A non-exhaustive list of types of trading includes:
- Long orders
- Short orders
- Etc…
Purpose #3 — Manage orders after submissions
The 3rd purpose of DAM is to manage the orders after they are submitted. This includes:
- Recording all profits and losses made
- Logging all transactions
- Monitoring the unfulfilled orders.
In the following we will focus on the interaction between agents and the decision-making process.
We consider a set of autonomous trading agents:
- Moving Average AA (MA-AA) uses moving average strategies to predicate on the relationship between a security’s price and its moving average trend-line.
- Stochastic Oscillation AA (Sto-AA) implements a stochastic oscillation trading strategy to follow security price momentum.
- Risk AA (Rk-AA) assesses the risk that is inherent to all trading strategies.
- Voting AA (vAA).
- Trading AA (tAA).
Figure 5 shows the sequence of steps in decision making.

Decision Making Using Human Profiles
In this section, an evaluation protocol is described in which the user, here a human trader, reviews historical data set and answers questions related to trading strategies. The financial time series and the trader’s answers are stored on a database (DHT+blockchain) and are later used for decision making. The experiment aims at assessing the similarity between past and actual observations, and to take future decisions based on past experiences. For the sake of reproducibility, a large sample should be used.
Table 3 shows a small sample of questions to assess trading strategies.
MyProfile is a hypothetical dedicated interface that uses the blockchain to store historical time series and their quantitative indicators (Moving Average, Stochastic Oscillator, etc…), and the answers provided by the human traders.
The questionnaire phase occurs after the deployment phase and before the running phase. During the running phase, the DAC will apply feature extraction (MA, Stoch.) and similarity search for time series data.
Finding the degree to which a given time series resembles another one has been an active area of research for a number of years, and a great variety of techniques currently exist for measuring the similarity between time series data-sets.
Our objective is not to present an exhaustive review of the several dissimilarity measures that have been proposed. Classical metric parameters include:
- Euclidean distance,
- Dynamic Time Warping (DTW). DTW works by optimally aligning the time series in the temporal dimensions so that the accumulated cost of this alignment is minimal,
- Etc…
Each of these metric parameters will give an insight into the degree of similarity between the time series. Those indicators/statements can sometimes be contradictory, e.g. Euclidean distance may indicate that the signal resembles template 1, while DTW indicates that correlation is higher with template 3.
The size of the phase space — the set of the metric parameters — may contain a large number of dimensions, thus a clustering algorithm, such as k-means, may be better suited to assign a cluster to the data point. In addition, if the distance of the data to the centroid exceeds a threshold value, the DAC can take the decision to not cast the AA vote and to request human votes.
Due to of the size of the phase space, that is the number of metric parameters, a clustering algorithm, such as k-mean, may be use to assign a cluster to the data point. If the distance of the data to the centroid exceeds a threshold value, the DAC can request human traders to vote.


Decision Making With Neural Networks
In this section, an innovative approach is presented to decision making using a deep learning algorithm.
Instead of using deduction or a collection of rules, neural networks (NNs) rely on the ability to recognise patterns through experience. Although NNs are considered essentially adaptive pattern recognition, several researchers have applied NNs to business decision making situations in the past.
The available settings on NN architectures enable the user (human or artificial) to design sophisticated structures having incredibly rich and intelligent behaviours. For example, the user can:
- Standardise the input variables or the target variables,
- Specify the error function, the type of transfer, the activation functions,
- Add hidden layers,
- Etc…
Our objective is not to present an exhaustive review on NN architecture but to show, based on simple NN model, that neural network approaches can be used for voting making problems.
For the present problem, the input data vector that feeds the NN may consist of
- Boolean variables (True/False) corresponding to MA signals (Sell/Buy)
- Numeric values (momentum or price velocity)
- Stochastic oscillator indicators (Overbought/Oversold)
- Etc…
The architecture of the network proposed here is very simple. It consists of a single layer of input nodes and one output node (see Figure 7)


The first phase will consist on training the DAC. A trend-oriented training in parallel to a forecast-oriented training should be developed to enhance the predictions of stock market trends. Predefined trend targets based on moving average, stochastic oscillator, etc. are used for machine learning, and metric indicators such as Bias, MACD, etc… and their combinations are chosen as input signals to the system. The potential output may be the categories {buy, hold, sell}. This trend-oriented training gives the system reliable learning targets to capture dynamic price trends.
Working with Contract — Pay for Performance
Example: Someone submits a proposal to build Martian space stations. We are going to need a range of technology, skills, and services to implement that proposal:
- Web designers and web development specialists to get creative crowd-funding website
- Project managers, architects and developers to design and implement the project
- Either acquire existing Martian space stations from an existing provider or build our own
- Use cryptocurrency for payments to services and goods
- Etc…
Appendix 1

References
[2] http://bitcoin.stackexchange.com/questions/2376/ecdsa-r-s-encoding-as-a-signature
[3] http://github.com/czielinski/secmultipartycomp/blob/master/slides/sec_multi_party_comp.pdf
Notes
[1] Online ratings sites can be used to provide trustworthy information.
[2] Table 4 shows as an example a checklist for assessing subcontractor quality. The score reflects the commitment of the contractor to established quality principles.