Iron is a pure chemical element as well as being a rather malleable metal. It may be better than many forms of metal we used in history, but it remains too soft or too brittle for many applications, and this is especially true in the case of tools and if you want a knife that is to be sharp. This is where iron and steel differ, steel can maintain an edge, and it can be created in many forms that are far more resilient than iron. Steel, however, is mostly iron with a few imperfections, not many, but enough to have the structure of the compound altered sufficiently such that it reacts on a fundamentally different level.
This is analogous to bitcoin.
Bitcoin is not a pure system; it has what most mathematicians and computer scientists see to be flawed. That said, these “flaws” are what makes bitcoin strong.
Orphans and plans to limit the creation of orphan blocks
Many developers think that Orphan blocks are a primary concern that needs to be address and worse, fixed. Orphans are not a flaw; they are the carbon introduced into the Iron that makes Bitcoin steel.
The way that bitcoin works leaves the creation of orphan blocks irrelevant to the overall reward structure. This is a consequence of the difficulty adjustment. Every two week, a mean (average) of around 2,016 blocks are discovered by miners. This is not orphan blocks but awarded blocks.
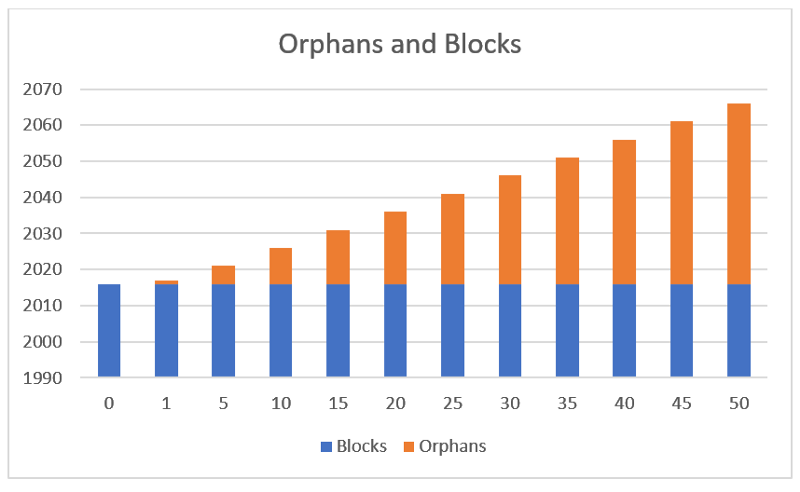
Let us put this into perspective with a table showing the orphans to miner reward level on average.

You will notice, the orphan blocks change nothing. We see this in the graph displayed below.

We see from this that the block rewards for a miner remain the same on average no matter how large the orphan rate. So, as Adam Smith said;
People of the same trade seldom meet together, even for merriment and diversion, but the conversation ends in a conspiracy against the public, or in some contrivance to raise prices…. However, though the law cannot hinder people of the same trade from sometimes assembling together, it ought to do nothing to facilitate such assemblies, much less to render them necessary.
The Wealth Of Nations, Book IV Chapter VIII, p. 145, para. c27.
Moreover, in Bitcoin, when they do, miners talk of their perceived losses, not that which is real, but what they see and note and feel through a single loss and do not consider the whole. In Bitcoin, miners talk of Orphaned blocks as they do not see that this is the desired state and they have been taught that it is not desirable. That, if these are removed, then somehow, they will earn more. That is the lie and the falsehood we must address.
Moreover, we see the same effect in the move to make orphan blocks less again from the meetings of those in business from the time of Adam Smith again:
To widen the market and to narrow the competition, is always the interest of the dealers…The proposal of any new law or regulation of commerce which comes from this order, ought always to be listened to with great precaution, and ought never to be adopted till after having been long and carefully examined, not only with the most scrupulous, but with the most suspicious attention. It comes from an order of men, whose interest is never exactly the same with that of the public, who have generally an interest to deceive and even oppress the public, and who accordingly have, upon many occasions, both deceived and oppressed it.
The Wealth Of Nations, Book I, Chapter XI, Conclusion of the Chapter, p.267, para. 10.
Business as miners see the losses they make, but rarely think beyond this, and when, told by those with good intentions (and we know where these usually lead) that this can be solved, listen to a tail that leads to ruin.
The simple truth is that Orphan blocks and the supposed flaws are a key element that makes Bitcoin work. It is not a thing to be fixed, to make it more efficient, it is a critical aspect, that if removed will allow the collapse of the system.
Bitcoin is Biologically inspired.
Orphan blocks aid in the competition within Bitcoin as a system. Bitcoin is not designed to lead to equal distribution, it is designed to create a competitive system that has miners and businesses striving to gain any edge they can, it is a system with competition in its very heart, and it does not work in any other form.
Bitcoin requires a level of inefficiency as Orphans align miners. It helps to sort them and ensure that they are correctly aligning their resources to ensure not only hash power but the distribution of connectivity and the investment in this vital aspect of the system. Orphans help miners sort the investment into resources. That is, the creation of an orphan block incentivises a miner to spend more money and capital ensuring that they are densely connected to the other miners.
All these things help all miners. However, like all things in business, most think of the short-term and see that which they lost and not the overall system.
I recommend a reading of the following text.

A game model for this aspect of the miners’ interactions is a “Stag Hunt”. This was based on Jean Jacques Rousseau’s postulations of a co-operation strategy between two hunters (Skyrms, 2004). These individuals can either jointly hunt a stag or individually hunt a rabbit. The most substantial payoff is assigned against the capture of a stag which provides a more substantial return than the hare. The hunting of a stag is more demanding and requires mutual cooperation. If either player hunts a stag alone, the chance of success is negligible and sub-optimal. Hunting stags is most beneficial for society in that this activity creates the optimal returns. The problem with this game in systems more generally is that it required too much trust among the players.
Bitcoin changed this through the introduction of asymmetries. It costs incrementally different amounts for different actions and costs more to deviate from the “honest” strategy than it does to attack. That is, we have introduced incentives to make it more likely that miners act to hunt a stag and make the network secure than they do if they defect and seek small gains. The system rewards miners for being “honest”.
This game has two pure strategy equilibria in which both players (miners) prefer the lower risk equilibrium to the higher payoff equilibrium. The game is both Pareto optimal and Hicks optimal, but the sub-optimal and hence inefficient equilibrium poses a lower risk to either player. As the payoff variance over the other player’s strategies is less than that of the optimal solution, it is more likely that this option will be selected. Another way of stating this is that the equilibrium is payoff-dominant while the other strategy is risk-dominant.
This is a problem with these game forms. To mitigate the risk-reward dilemma, Bitcoin has introduced a long play asymmetry that increases over time and against investment. The payoffs in connectivity allow a densely connected system at a cost and risk position that is lower than should be expected.
The strategy between the miners incorporates a conflicting choice of increasing hash rate against increasing connectivity. We display this in Figure 3, the numerical representations represent the payoff figures for the specific case (the mining competition market) and the generalised relations take the form:

The outcomes are not definitive statements of what will be produced. In this game, the “Stag” is a desire to “Create a near complete, small world network” and the “Hare” the fall-back to adding more hash power (i.e. an increased investment in ASICs). A desire is not a case of creating a more densely connected network between miners by itself, but rather a combination of adding ASICs to increase the miners hash rate and maximising the connectivity of the system. At some point, more network connectivity adds little if anything to the miner’s profits and at another, it is more hash rate that is more effective as an investment.

The payoffs for creating more densely connected systems are significant for both the miners and the user in Bitcoin, but the risk of a misaligned strategy leads to the sub-optimal equilibria. What is needed is a signalling process. A signal will allow the players to align with the more optimal strategy. It is not only in the user’s interest to have more a secure system (more densely connected), but also is in the interest of the miner. Orphans are expensive for the individual miner experiencing these (though, not a cost to the network as a whole) and the better-connected miner can reasonably expect a lower orphan rate and more blocks to be won.
As the ratio between the payoff for stag hunting and the payoff for hare hunting is reduced, the incentives to move towards stag hunting decreases. As a result, it becomes less likely that more connectivity will be made into a primary goal of either miner. It is hence less probable that an alteration of the player’s strategy from hare to stag will come without the costs of orphaning blocks for the miner.
Since neither player has an incentive to deviate, this probability distribution over the strategies is known as a correlated equilibrium of the game. Notably, the expected payoff for this equilibrium is 7(1/3) + 2(1/3) + 6(1/3) = 5 which is higher than the expected payoff of the mixed strategy Nash equilibrium.
Miners can determine the costs associated with each strategy readily. This is signalled though a combination of profit and orphans (and the associated losses that come through individual miners having blocks orphaned).
Miners need to compete.
Each miner needs to be better but not as a system. That may be counter-intuitive to many developers and engineers, but the system is designed such that each miner fights to be better connected to the complete set of miners. They compete to be more closely linked and more densely connected with lower latency. If a miner has a lower latency, that miner can gain a fractional percent gain over another miner.
Conversely, if the network is more effective and efficient, Sybils act at a lower cost. This may help home users and Raspberry Pi machines, but not those with Skin in the Game. Bitcoin is not designed to have demagoguery where you vote without any interest in what you vote on. That is twitter, and it breeds trolls and those who have no interest in the system.
When we make bitcoin more efficient, it allows more systems to act as forwarders and to connect to the network without needing to spend as much on connectivity. This allows those who are not miners to start acting and pretending to be nodes at a lower cost.
Several Microsoft researchers correctly summarised a problem with Blockchains (and this applies to many that exist now, such as Ethereum) in “On bitcoin and red balloons” [2]. These authors never tested the system. They failed to investigate how Bitcoin works and assumed a mesh network. Others utterly failed in their understanding of Bitcoin (again looking at mesh structures) and proposed infeasible attacks based on Sybils propagating and taking over to “selfish mine”.
Mining is not about discovering blocks; it is about getting your discovered block to all other miners. This is a critical distinction. It is not merely an investment in ASICs to capture hash power, but also a suite of other parts. Miners need to:
1. Ensure security,
2. Have good network management systems,
3. Have high bandwidth low latency connectivity to other miners,
4. Redundancy,
5. Dense network connectivity to many places allowing a flood of blocks and TXs into their systems and node.
This is created using an asymmetric game.
The cost for an attacker is far more significant than it is for the honest miner. The cost to a miner to connect to all other nodes is a part of the system. There is an optimal point where adding more connectivity becomes less profitable. This may be at 98% or 99% or more connectivity and will vary based on the individuals miners costs, but this cost is asymmetric against the costs of both ASIC hardware and attacks.
A miner can handle connectivity at 4 GB Blocks easily with a 10GbE Internet network. I have one of these at home. This is not particularly special these days, and any decent datacentre has far greater connectivity.
The costs for a 0.1% miner to install the connectivity to allow a 1GB block to get to 1,000 miners in a densely connected system in under 2 seconds comes to under 1% of the capital investment needed by the miner. For a set of Sybil nodes attacking the system, this level of connectivity increased the costs between 9 to 10 x that of an attach using a meshed network and lower connection needs.
This is how the system is asymmetric.
To attack a miner, you need to invest money into a system that requires a long-term capital investment. This is not simply buying a set of ASIC miners and connecting to a pool. That pool has to have the required infrastructure to allow the pool members to earn without losing blocks and pool miners can generally switch easily between pools. So, a pool that seeks to exploit its position is soon to be a bankrupted pool.
An attacker needs to be able to have more edges (unordered pairs of vertices or nodes, that is, the links between the nodes) than the rest of the network. Worse, it is not just having more; it is a requirement to have massively more edges on the network. So, if we have a network of 1,000 miners densely connected, an attacker would need to run up over 500,000 densely connected systems to act as Sybils to be able to have an equal effect as the honest mining nodes and this without earning as the miners do.
The costs of such an attack today exceed 125 Billion USD to complete. It is not only running up a few Raspberry Pi (UASF) nodes but real densely connected low latency systems. This is a substantial investment, not in a few virtual machines, but a complete dense infrastructure that requires a long-term investment as other miners see to favour connections to your node. Hence, any attempt to attack the network also suffers from the requirement not only to invest in an instant attack, but to create a long-term investment, to gain and build up trust between the other miners, to send blocks and to seem as if they are a competent member of the mining “community” before burning all that investment and seeking a quick, and easy to filter attack that can be mitigated in minutes.
Alice and Bob as miners.
If we take a small sample as a hypothetical subset of the network, Bob and Allice the miners say, and we assigned them each an equal level of hash power, we can start to explore what connectivity and latency mean for Bitcoin. We will for this example set Alice and Bob with 50% of the overall network each. This is not realistic but let assume that Alice and Bob are two sets of miners with different strategies.
We start with Alice, she and Bob each have 1,000 units of hash power. Alice has invested in systems, infrastructure and network pipes that allow her to connect to all other miners with a latency (even at large blocks) of under 0.2 seconds.

Bob has decided not to spend as much on his network infrastructure and has a latency for large blocks of 3.2 seconds. This is not an enormous difference, but let’s investigate the impact.
Ceteris paribus (or taking all other things to be equal in economist-speak), we have a block time of 600 seconds on average. The time difference experienced between Alice and Bob for getting blocks out is 3 seconds (3.2–0.2) or 0.5% (3/600) as a gain to Alice. This means Alice is in effect acting as a 50.5% miner and Bob is now a 49.5% miner. From an equal position, Bob is now losing a small amount to Alice.
For Bob to gain this level of advantage even using ASICs alone, he will need to spend significantly more.
If Bob installs 21 more ASIC units, the mix is now:

Notice how Bob has needed to expend 2.1 % more using an investment in ASICs and gained 0.5% whereas Alice has invested what comes in current terms to a smaller investment in network infrastructure and the real effect of the system is now:

As we see the hash rate of the network increase, the costs of scaling bandwidth become less expensive compared to the costs of increasing hash power. This is one of the asymmetric effects of Bitcoin.
It is one of the controls that are broken and made not to function if the system becomes more efficient. Bitcoin is a very carefully constructed system of incentives and controls. As I have stated many times, it is an economic system that utilises selected cryptographic tools; it is not a cryptographic system.
Miners are incentivised to increase the connectivity of the system to a point where losses from orphans are low to them. This is not a gain if it is conducted as a change to the overall system. Making the system more efficient lowers the asymmetry in the system allowing attacks and lowering the incentive to connect as a small world rather than a simple mesh.
Competition, not social consensus
Bitcoin did not fail and miss social consensus; it was designed to not fall into this trap. There is no such thing as a robust system built on social consensus. The reason is incentives. If you do not need to invest in the decisions you are making; you do not care to spend the time understanding them. This is the failure of democracy and why it often leads to demagoguery. People do not have skin in the game and have little of their own to risk.
Bitcoin functions as the participants, them miners and the enterprises in the system all have Skin in the Game. They all must invest. They all must risk losing all they have, and this means that they are always going to be required to investigate the decisions that are being made.
This was of course not always the case. In the early days of Bitcoin, the value ration was too low. That point is not sustainable and will never lead to a system of global cash, it cannot be more than a toy system, and this has led many people to miscomprehend bitcoin thinking that this is what it is designed to be.
Orphans are how miners vote
One last point I have to make a note of. This is that orphan blocks are also the means for miners to vote and accept fees, valid blocks, or anything else they seek to enforce as an emergent market.
This is the ONLY way that miners can honestly vote.
[Miners] vote with their CPU power, expressing their acceptance of valid blocks by working on extending them and rejecting invalid blocks by refusing to work on them. Any needed rules and incentives can be enforced with this consensus mechanism.
Bitcoin Whitepaper
To conclude… (for today)
This shall be the first in a (long) series of articles designed to start explaining some of what people see to be flaws in Bitcoin and how these are in fact the strength that allows it to grow and scale.
Bitcoin (cash) remains steel. In the last couple years, Bitcoin has remained steel as others have moved to increase their purity and seek “perfection”. Bitcoin Core in SegWit has made a strong move towards becoming pure iron. That is the failing of Core. Like iron, it is not strong enough to survive what is coming.
References
1. Smith, Adam. The Wealth of Nations: A Translation into Modern English, Industrial Systems Research, 2015
2. Moshe Babaioff, Shahar Dobzinski, Sigal Oren, and Aviv Zohar. 2012. On bitcoin and red balloons. In Proceedings of the 13th ACM Conference on Electronic Commerce (EC ‘12). ACM, New York, NY, USA, 56–73. DOI=http://dx.doi.org/10.1145/2229012.2229022
3. Skyrms, B. (2004). The Stag Hunt and the Evolution of Social Structure: Cambridge University Press.
4. Bitcoin Whitepaper